Today's world, Security is the most important thing in all places. There may be lot of loop holes to hack it. So to identify the loop holes there are lots of tools are available in the market.Today we will see a tool called "kube-hunter" its an open source tool developed by Aqua Security to identify the security issues in Kubernetes clusters. Through this tool we can identify open security issues.
Here am going to explain how to use this tool,
Requirement :
Python : 3.X
Pip : 3.x
OS : Centos 7.6
I have a running Kubernetes cluster already to use this tool.
Installation :
Clone the git repos. of kube-hunter.
# git clone https://github.com/aquasecurity/kube-hunter.git
# cd kube-hunter
# pip install -r requirements.txt
Kube-hunter Scanning :
Once the pip installtion is done, now we can run the this tool to identify the security flaws in Kubernetes cluster.
# cd kube-hunter
# ./kube-hunter.py
It will ask for 3 options like below,
1.Remote Scanning : It will scan the Kubernetes remote cluster with IP/DNS.
2.Interface Scanning : It will search and scan the kubernetes cluster on all local network interfaces.
3.IP Range Scanning : It will search and scan Kubernetes cluster with the given IP range.
For example, I have chosen remote scanning no. 1 and given my local kubernetes cluster IP for scanning and below the results,
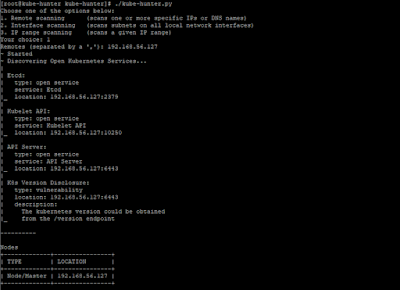

It has found one vulnerability that "The fact that your infrastructure is using Kubernetes, and the specific version of Kubernetes used is publicly available, and could be used by an attacker to target your environment with known vulnerabilities in the specific version of Kubernetes."
The results may vary in each environment.
We can run the scan directly by,
# ./kube-hunter.py --remote Kubernetes_IP/Domain
or
# ./kube-hunter.py --interface
or
# ./kube-hunter.py --cidr 192.168.0.0/24
Active Hunting :
Active hunting is an another option to find more vulnerabilities in Kubernetes Cluster. The difference between normal(above one) and active hunting is that a normal hunt will never change state of the cluster, while active hunting can potentially do state-changing operations on the cluster, which could be harmful.
By default, kube-hunter does not do active hunting.
To check the Kubernetes cluster with active hunt use below example.
# ./kube-hunter.py --remote Kubernetes_IP/Domain --active
Thats all, Kube-hunter has been installed and checked the security issues in Kubernetes Cluster.



Post a Comment